Data Security and Privacy
- Home
- Data Security and Privacy
Sensitive data protection, intelligence, and management
Data security and privacy challenge organizations to meet different but very critical and complementary issues: Data security governs access to data throughout its lifecycle, whereas data privacy defines that access based on privacy policies and laws—for instance, who views personal, financial, health, or confidential data. Both are challenged today with the growth and proliferation of data from cloud, analytic, and big data initiatives, and the continued barrage of data breaches.
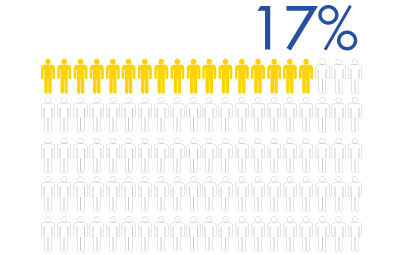
According to the Ponemon Institute’s “The State of Data Centric Security” fewer than 1 in 5 IT practitioners knows where structured data is located.
Traditional security needs data-centric security
The implications and costs of security breaches are front-page news and encompass everything from loss of jobs, to loss of revenue, to PR nightmares. As the volume and proliferation of data from cloud to mobile to social to machine continues to grow, traditional security approaches no longer deliver safe harbor for sensitive data.
As attacks become more persistent and sophisticated, traditional security measures will be breached—and it is not “if,” but “when.” When that happens, additional safeguards are needed for protecting sensitive information. And you can’t protect data if you don’t know where it is. According to a recent Ponemon Institute report, only 17 percent of IT practitioners know where their company’s sensitive structured data is located. Only 7 percent know where their unstructured data resides.
While the exponential increase in the volume and proliferation of data creates significant risk, companies that focus on securing the data itself will triumph in the fight for data security.
When choosing a data security solution, look for the following attributes:
- Accessible: Make sure your solution can access data wherever it is, whether it’s in new data channels, your mainframe, or your line-of-business application. With the ever-growing data volume and variety, sensitive data must be protected and understood, regardless of its origin.
- Unintrusive: Solutions should work within existing architectures and not require changes to proven and reliable databases and applications.
- Deployment-agnostic: Your solution should have the ability to access a wide variety of deployment models, from big data to cloud to on-premises to hybrid ecosystems.
- Technology-agnostic: Whether you’re using a legacy system or state-of-the-art innovation, your solution shouldn't require a change in applications and databases to align with the newest technology.
- Adaptable: You want a platform that can handle a wide variety of use cases—from blocking access to fine-grain control with a single approach.
